Datasets
ADOC - An Anomaly Detection Dataset for Events in a Single Camera.
Anomolous events: Given all events that may occur in the view of a surveillance camera, one would like to analyze the video to identify a subset of events (anomalous) that require attention. Most methods have defined anomaly as a deviation from the normal. Given all observations that may occur and their frequency of occurrences, normal events can be defined as those that have a higher frequency of occurrence, and conversely anomalous eventsare defined as the complementary set of normalevents (those that have lower frequency of occurrence).
Data: The data is acquired from a surveillance camera deployed on a large university campus. It overlooks a walkway leading to various buildings and captures the events performed by students, faculty , and staff on a busy day. The camera captures video at a resolution of 1080p and a frame-rate of 3 frames per second. The video is compressed using H.264 format, which is a lossy compression method and is standard of the surveillance industry. We create a dataset from video captured over a period of 24 contiguous hours. The video encapsulates varying illumination conditions, crowded scenarios with background clutter. The data is annotated with a number of events ranging from low to high frequency.
Events: A total of 875 events are annotated, the top 5 events are shown in table below.
| Event Name | Frequency |
|---|---|
| person riding a bike | 238 |
| person on grass | 132 |
| golf cart on walkway | 105 |
| having a conversation | 58 |
| person on skateboard | 48 |
 Peson Riding a Bike
Peson Riding a Bike Peson Riding a Bike (Night)
Peson Riding a Bike (Night) Person Walking on Grass
Person Walking on Grass Golf Cart on Walkway
Golf Cart on Walkway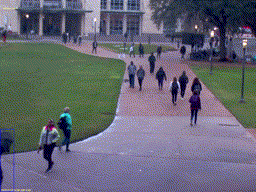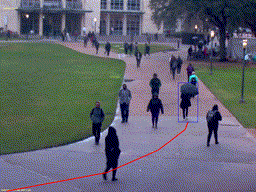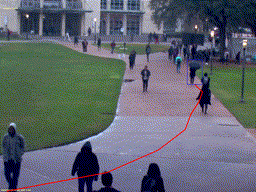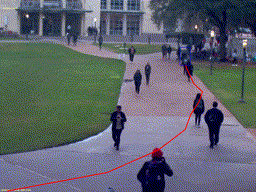 Person with Umbrella
Person with Umbrella Having a Conversation
Having a Conversation Person on Skateboard
Person on Skateboard Person on Mobility Scooter
Person on Mobility ScooterResources:
Please cite the paper Mantini Pranav, Li Zhenggang, Shah Shishir K; A Day on Campus - An Anomaly Detection Dataset for Events in a Single Camera. In Proceedings of the Asian Conference on Computer Vision (ACCV), 2020
Paper download link
The download link contain.
1. adoc_v.1.1.zip (2GB): Contains the dataset
Please fill the agreement form to download dataset.
Camera Tampering: An unauthorized or an accidental change in the view of a surveillance camera is called a tampering. This can be the result of a natural phenomenon or it can be induced to accomplish malicious activities. Figure 1 (a) & (b) shows an example of tampering due to a natural phenomenon, where the sunlight is reflected on to the camera lens. Figure 1 (c) & (d) shows anexample of tampering induced by a hu- man. The perpetrator blocks the view of the camera using a cardboard. Images Figure 1 (b) & (d) are compromised and may not be useful for surveillance. Another example is of natural tampering would be when cameras switch between day/night mode. Often cameras fail to auto-focus correctly after switching between day/night mode resulting in a defocussed view.Examples of unauthorized tampering would include spray painting the lens, changing the viewpoint intentionally to accomplish malicious activities (such as theft and property damage).
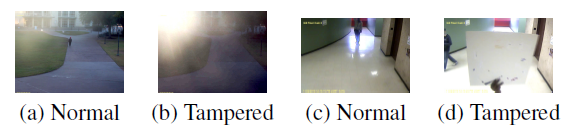 Figure 1: Example of natural tampering due to reflection of sunlight on to the camera lens (a) & (b),
Example of inten tional tampering due to a covered lens (c) & (d)
Figure 1: Example of natural tampering due to reflection of sunlight on to the camera lens (a) & (b),
Example of inten tional tampering due to a covered lens (c) & (d)
Most literature has classified camera tampering as covered, defocussed, and moved. Covered tampering occurs when the view of the camera is blocked. Spray painting the lens, blocking it with hand, and accumulation of dust, spider webs, and droplets are exam- ples of covered tampering. Defocussed tampering occurs when the view of the camera is blurred. Formation of fog on lens, failures to focus, and intentionally changing the focus are examples of defocussed tampering. Moved tamper- ing occurs when the view point of the camera has changed. This can occur as a result of strong wind, an intentionally change in the direction of the lens with malicious intent.
UHCTD is a large scale synthetic dataset for camera tampering detection. The dataset is created from two outdoor surveillance cameras, Camera A and Camera B, the viewpoints fore each are shown in Figure 2 Row 1. Camera A has a resolution of 2048X1536, and Camera B has a resolution of 1280X960.The videos are cropped to a 3 rd of their resolution during synthesis. Camera A has a framerate of 3 frames per second (fps), and Camera B has a framerate of 10 fps. The two cameras together capture a wide variety of regular scene changes that occur in surveillance cameras.
 Figure 2: Row 1: Cam A & Cam B viewpoints; Row 2: Natural illumination changes in camera A; Row 3: Illumination
changes due to shadow in Cam B; Row 4: Illumination changes due to weather in Cam A; Row 5: Crowded scenarios in
Cam A & Cam B; Row 6: Extended periods of scene change in Cam A.
Figure 2: Row 1: Cam A & Cam B viewpoints; Row 2: Natural illumination changes in camera A; Row 3: Illumination
changes due to shadow in Cam B; Row 4: Illumination changes due to weather in Cam A; Row 5: Crowded scenarios in
Cam A & Cam B; Row 6: Extended periods of scene change in Cam A.
We define four classes: normal, covered, defocussed, and moved. The tampers are synthesised into the videos using image processing techniquies.
 Figure 4: Synthetic Data. a) Original, b) Covered, c) Defocussed, and d) Moved images.
Figure 4: Synthetic Data. a) Original, b) Covered, c) Defocussed, and d) Moved images.
Resources:
Please cite the paper Mantini, P., Shah, S. K. (2019, September). UHCTD: A
Comprehensive Dataset for Camera Tampering Detection. In 2019 16th IEEE International Conference on
Advanced Video and Signal Based Surveillance(AVSS). IEEE
Preprint paper download link
The download link contains two folders.
1. UHCTD.zip (26GB): Contains the dataset
2. groundtruth_and_predictions.zip (25MB): Contains the annotaion and prediction files to reproduce results from the folder
Please fill the agreement form to download dataset.
Github: Code to train and predict using alexnet, resnet18, resnet50, densenet161 is availble on Github. CTD-Devkit, Download UHCTD.zip
Github: Code to reproduce results from the paper is available on github. CTD-Evaluation, Download groundtruth_and_predictions.zip